Using Microsoft Graph
Microsoft Graph can be used together with the On Behalf Flow (OBO), but in order to make this work you must alter your app registration configuration a bit.
info
This documentation is based off issue #40
Backend API App Registration
- Head over to Azure -> Azure Active Directory -> App registrations, and select your Backend API Application Registration
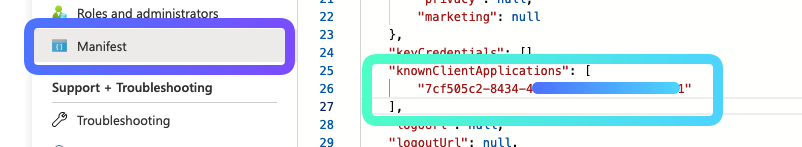
- Navigate to the
Manifestin the menu on the left - Add your OpenAPI/Swagger ClientID to the
knownClientApplications(saved asOPENAPI_CLIENT_IDin your.env)
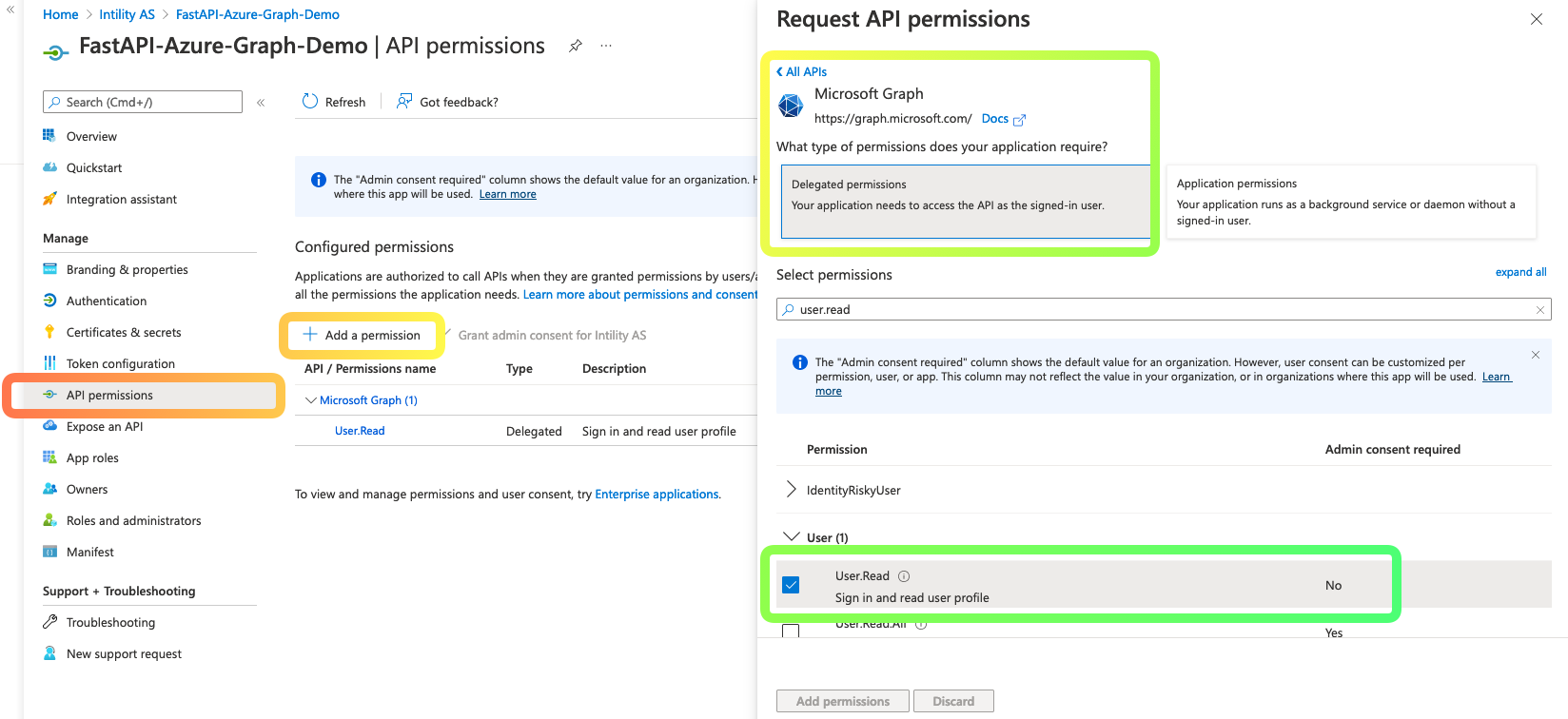
- Select
API permissionsand ensureUser.Readis there. If not, follow the steps in the picture below:Add a permission- Select
Microsoft GraphunderMicrosoft APIs - Select
Delegated permissions - Search for and select
User.Read - Click add permission
- Select
Certificates & Secretsand create a secret for your backend to use in order to fetch a Graph tokenNew client secret- Give it a name
- Add
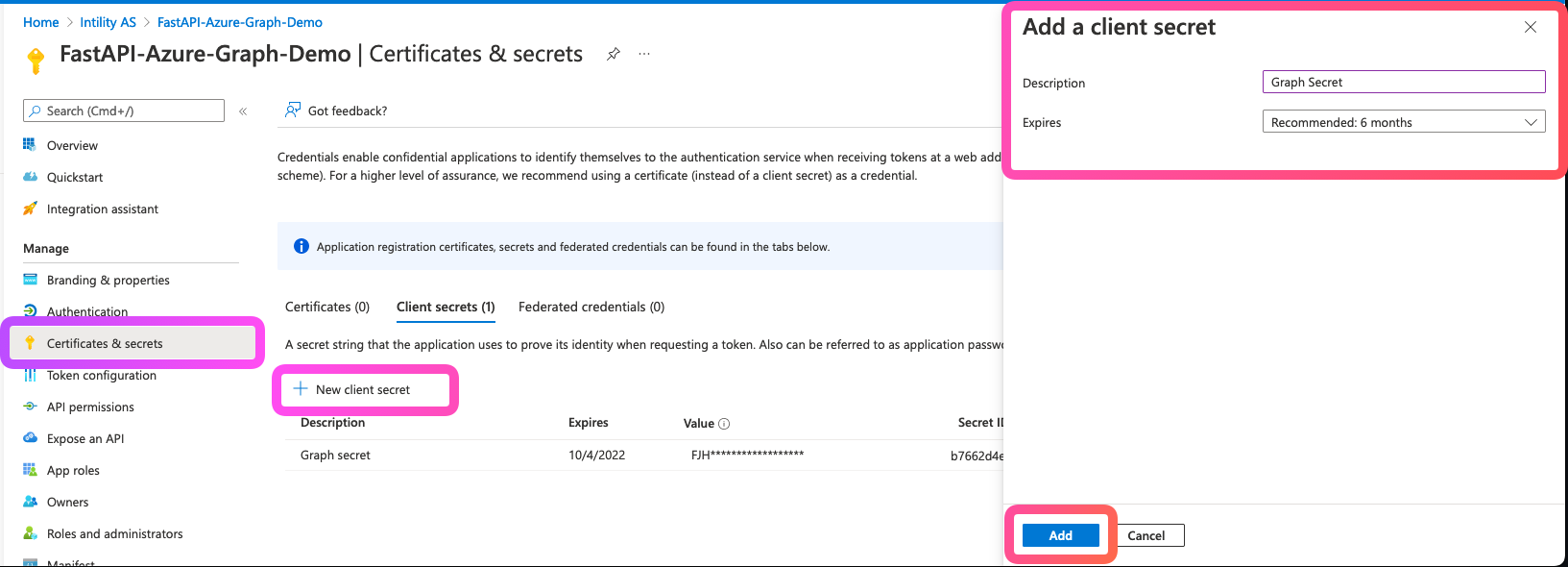
OpenAPI App Registration
- Head back to Azure -> Azure Active Directory -> App registrations, and select your OpenAPI/Swagger Application Registration
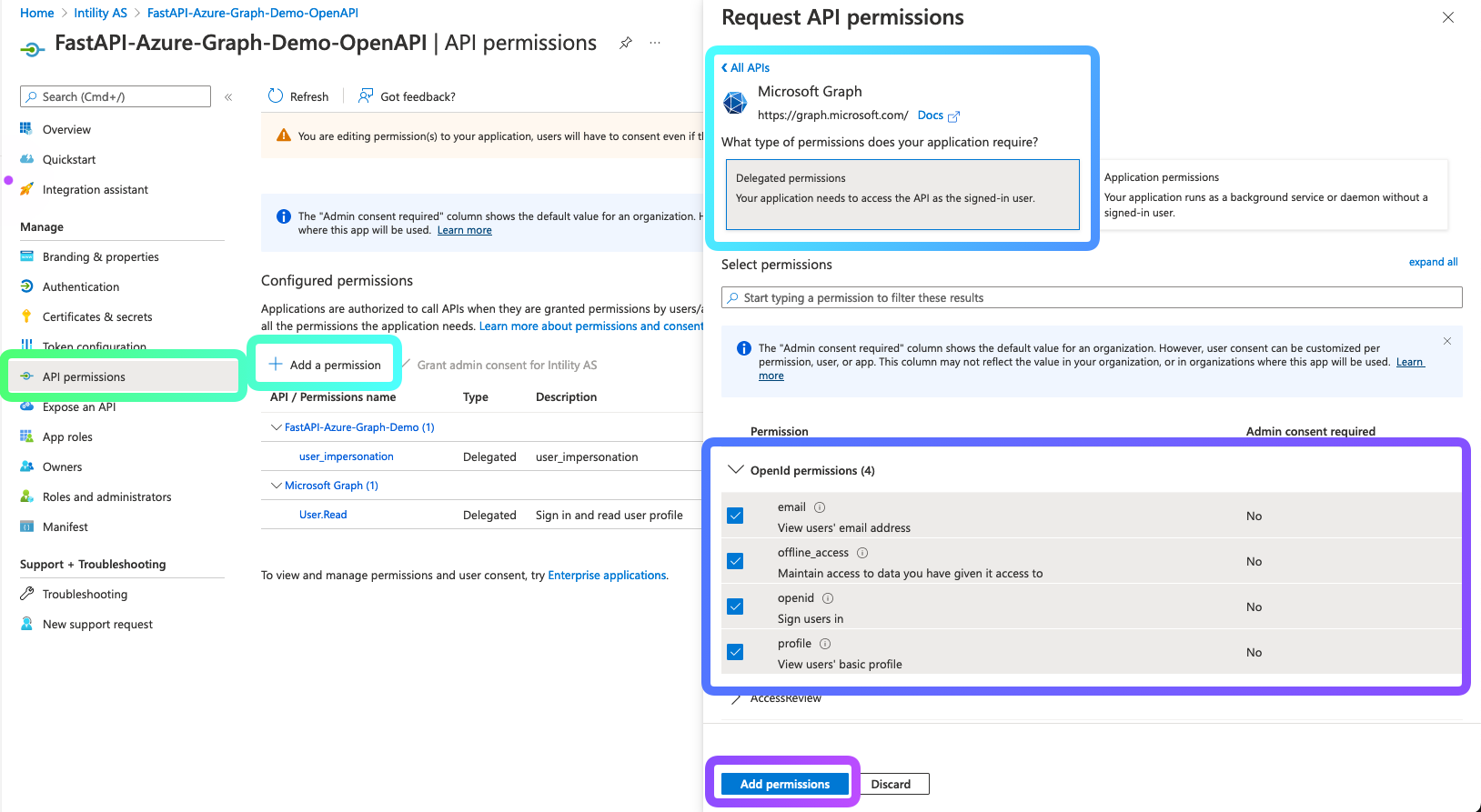
- Select
API permissionsin the menu on the left - Add
email,offline_access,openid,profilescopesAdd a permission- Select
Microsoft GraphunderMicrosoft APIs - Select
Delegated permissions - Select the permissions
- Click add permission
Code
You can now fetch a graph token using the OBO flow. A full code example of an API using Graph can be found in the demo project.